There are chances that you might have thought of being watched by US
government through Gmail, Facebook and other internet giants who are
holding your sensitive and most private data.
The news is that all your fears were real, as a new secret document has proven the existence of a US government program that grants NSA (National Security Agency) and FBI the direct access to the servers of Google, Facebook, Microsoft, Skype, Yahoo, Apple and other internet companies, from where they can extract any user information at their will.
Named as PRISM, the program was sanctioned by President Bush in 2007, which is now renewed again by President Obama in December 2012.
Under this program, tech giants gave the direct access to its servers to US government agencies, through which they can grab any information they want, without any hurdle.
The information that NSA can access may include your emails, chats, search history, images, videos, skype calls (even the content of skype calls), YouTube videos (even those which are private), files that are stored in your computer, call records of your smartphones, SMS, MMS, places you visit and much more.
Microsoft joined this program before anyone, followed by Yahoo and Google. Facebook, Skype, Youtube, AOL and Apple are also the program partners who have given the direct access and they can obtain information of any kind for any user who uses these services.
Dropbox is likely to be added in the list of partner companies soon.
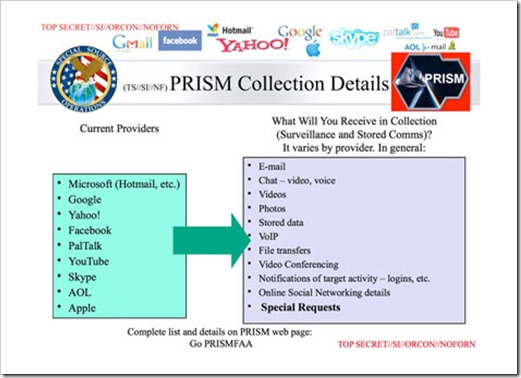
PRISM enables US government agencies to reach directly into the servers of the participating companies and obtain both stored communications as well as perform real-time collection on targeted users.
Interestingly, US agencies call PRISM “one of the most valuable, unique and productive accesses for NSA”.
Another fact, which may worry our local “Privacy and Internet Freedom Activists” to a greater level is that Pakistan is second largest spying target of NSA, after Iran. Over 13.5 billion reports were gathered from Pakistan in March 2013 only.
Given the amount of data we share with these companies, including our personal and private information, this revelation is alarming and raise countless serious questions, concerning the morality of tech companies and US government.
The news is that all your fears were real, as a new secret document has proven the existence of a US government program that grants NSA (National Security Agency) and FBI the direct access to the servers of Google, Facebook, Microsoft, Skype, Yahoo, Apple and other internet companies, from where they can extract any user information at their will.
Named as PRISM, the program was sanctioned by President Bush in 2007, which is now renewed again by President Obama in December 2012.
Under this program, tech giants gave the direct access to its servers to US government agencies, through which they can grab any information they want, without any hurdle.
The information that NSA can access may include your emails, chats, search history, images, videos, skype calls (even the content of skype calls), YouTube videos (even those which are private), files that are stored in your computer, call records of your smartphones, SMS, MMS, places you visit and much more.
Microsoft joined this program before anyone, followed by Yahoo and Google. Facebook, Skype, Youtube, AOL and Apple are also the program partners who have given the direct access and they can obtain information of any kind for any user who uses these services.
Dropbox is likely to be added in the list of partner companies soon.

PRISM enables US government agencies to reach directly into the servers of the participating companies and obtain both stored communications as well as perform real-time collection on targeted users.
Interestingly, US agencies call PRISM “one of the most valuable, unique and productive accesses for NSA”.
Another fact, which may worry our local “Privacy and Internet Freedom Activists” to a greater level is that Pakistan is second largest spying target of NSA, after Iran. Over 13.5 billion reports were gathered from Pakistan in March 2013 only.
Given the amount of data we share with these companies, including our personal and private information, this revelation is alarming and raise countless serious questions, concerning the morality of tech companies and US government.
































![WiFi wifi 300x189 Simple Wi Fi WEP Crack [TUTORIAL]](http://hackingarticles.com/wp-content/uploads/wifi-300x189.gif)